Secrets User Documentation
| Purpose | For working with sensitive data or keys, the Raven Portal uses something called Secrets, which helps the user work with more security by controlling access to crucial information. In this documentation, we will discuss in more depth what Secrets are, how to use them, and all the types of Secrets provided by the portal. |
|---|
| Created | August 28, 2024 |
|---|
What are Secrets
Secrets are sensitive keys stored securely, for usage within our Bricks. These are stored in a vault which will make the secret available for the team while keeping the credential data secure and easily manageable.
The vault is backend which means it works behind the scenes, the user can not actually see the vault in the Raven portal
Raven uses the "HashiCorp" vault, you can find more information about it in the following link:
General information about Secrets
-
To use Secrets in Bricks, they need to be centralized.
-
In order to achieve centralized control over our secrets we maintain a vault cluster.
-
Secrets run and scale in a dynamic cloud agnostic environment with frequently changing machines and network addresses.
-
Secrets can be managed from the portal without exposing their contents.
How to create a Secret
To create a Secret go to the settings which is located on the left column of the portal and select the "Secrets" option. At the top right corner the user will find the "ADD SECRET" button which will pop up a tab letting the user create a Secret.
Adding a Secret:
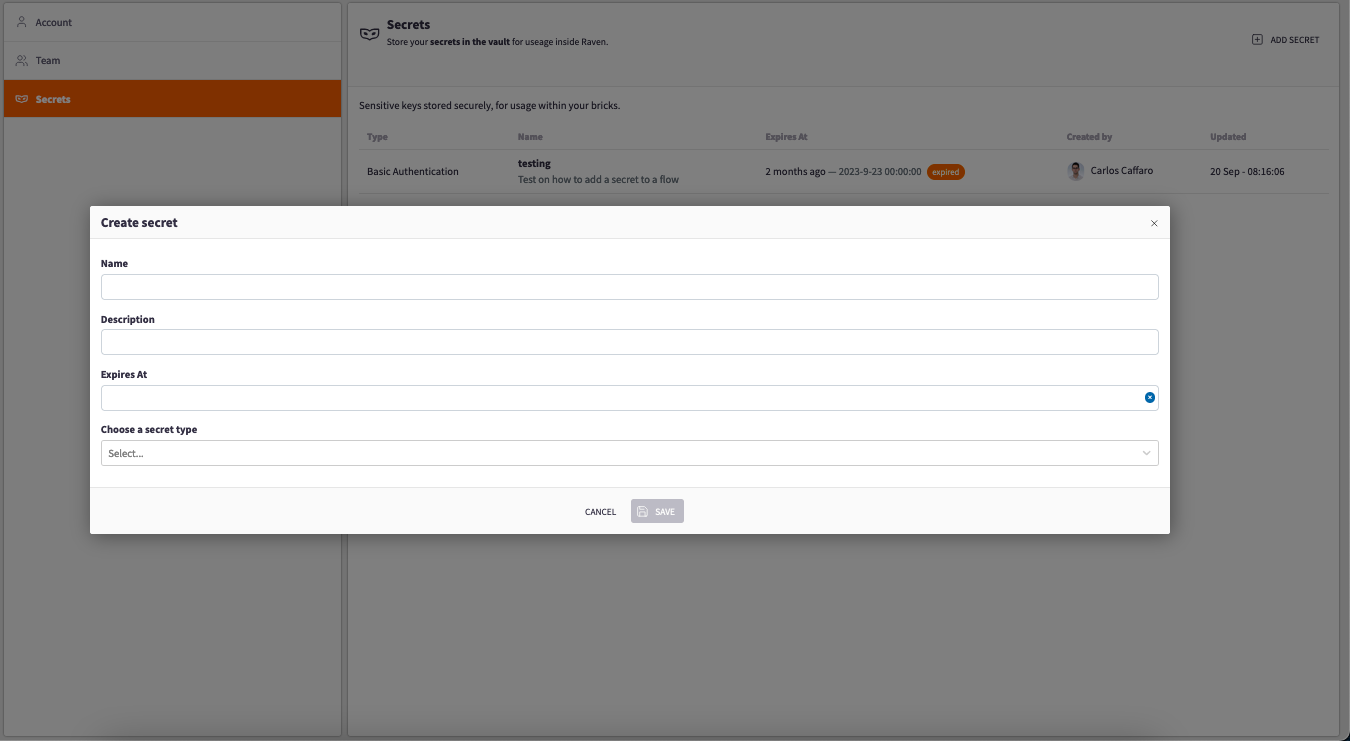
In this tab you will be able to set up four things:
-
Name
-
Description
-
Expiration Date: This allows you to define a time frame to use Secrets, keeping the data more secure
-
Secret Types: Will vary depending on what you have mentioned in the "Types of Secrets" section
After filling up this information press the "Save" button to create the Secret.
When creating a Secret it is recommended to use downscoped/permission credentials tailored to the specific task it intends to solve.
Some Secrets only apply for something specific like a region. Make sure when creating a Secret this specification is mentioned in the name or description of the Secret to avoid confusion.
Using a Secret
When a Brick parameter is in need of a Secret it contains a secret-select in the configuration window containing all available Secrets. Select the Secret for the Brick and finish the Brick's configuration.
Secrets can be used in four parts of the Portal:
-
Bricks: A Brick is a fundamental building block that performs specific tasks for event processing.
-
Flows: Raven Flows is an app that empowers users to perform Extract, Transform, and Load (ETL) operations on events. You can create custom Flows by chaining together individual Bricks.
-
Playbooks: Raven's Playbooks is a powerful app that allows you to create complex automated workflows by dragging and dropping Brick onto a canvas and connecting them together.
-
Tables: In Raven tables are used to organize and manage incoming data sources. A Table is essentially a collection of data that has been organized into rows and columns. Each row represents a single record, and each column represents a specific attribute or piece of information about that record.
These four concepts are explained with more detailed on their respective Documentation which can be found by clicking on the links:
Types of Secrets
There is not a right or wrong choice for Secrets; it depends on what you are trying to do. For example, if you need access to AWS resources, go for the AWS type. If you need a username and password for login, the BASIC type is the way to go, and so on.
Within this section, you will discover all the various types of Secrets that the Raven Portal supports. Beneath the Secret types, there is a link available to provide more details about that specific type.
BASIC, Basic Authentication
| Key | Label |
|---|---|
| USERNAME | "Username" |
| PASSWORD | "Password" |
oauth2client, OAuth 2.0 client credentials
| Key | Label |
|---|---|
| OAUTH2_CLIENT_ID | "Client Id" |
| OAUTH2_CLIENT_SECRET | "Client Secret" |
For more information on OAuth 2.0 follow link below:
AWS, Amazon Web Services
| Key | Label |
|---|---|
| AWS_ACCESS_KEY_ID | "Access Key" |
| AWS_SECRET_ACCESS_KEY | "Secret Access Key" |
For more information on Amazon Web Services follow link below:
[Learn more about AWS Security Credentials][https://docs.aws.amazon.com/IAM/latest/UserGuide/security-creds.html]
APIKEY, Api KEY
| Key | Label |
|---|---|
| API_KEY | "Key" |
Since every API Key is different on how to use them please follow the documentation provided by the specific company, organization or entity for more information.
Google, Google Service Account
| Key | Label |
|---|---|
| GOOGLE_SERVICE_ACCOUNT_JSON | "Private Key (json)" |
For more information on Google Service Account follow the link below:
Azure, Azure
| Key | Label |
|---|---|
| AZURE_TENANT_ID | "Tenant Id" |
| AZURE_CLIENT_ID | "Client Id" |
| AZURE_CLIENT_SECRET | "Client Secret" |
For more information on Azure follow the link below:
ConnectionString
| Key | Label |
|---|---|
| CONNECTION_STRING | "Connection String" |
Requesting new secret types
Customers can request new secret types as needed. If you want a new Secret type, reach out to your contact person for assistance and guidance.